@ariadne "No WAY the government will be able to read our chats now!"
@ariadne eeeeyupp,
the terraform provider creates and owns the channel. it is the only user with the right to turn on encryption for said channels. voila. this is a perfectly reasonable solution.
@ariadne I love it
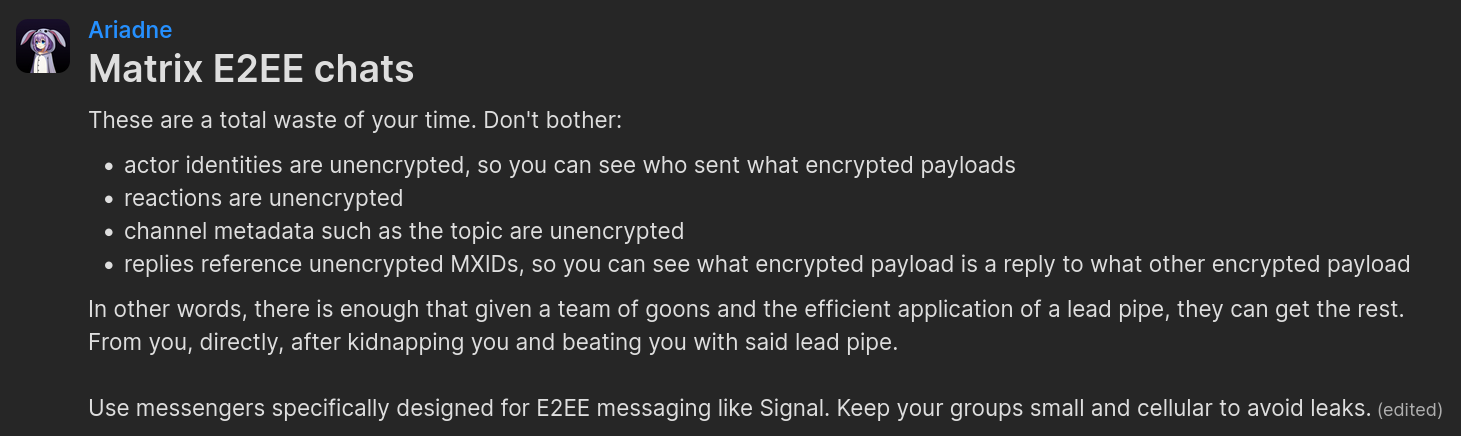
matrix E2EE channels are fucking stupid because they leak all sorts of metadata
for example, the topic is unencrypted
reactions are unencrypted
replies reference unencrypted MXIDs so you can tell what is being replied to even if the payload itself is encrypted
do not use them. do not waste your time on them. it is not worth it.
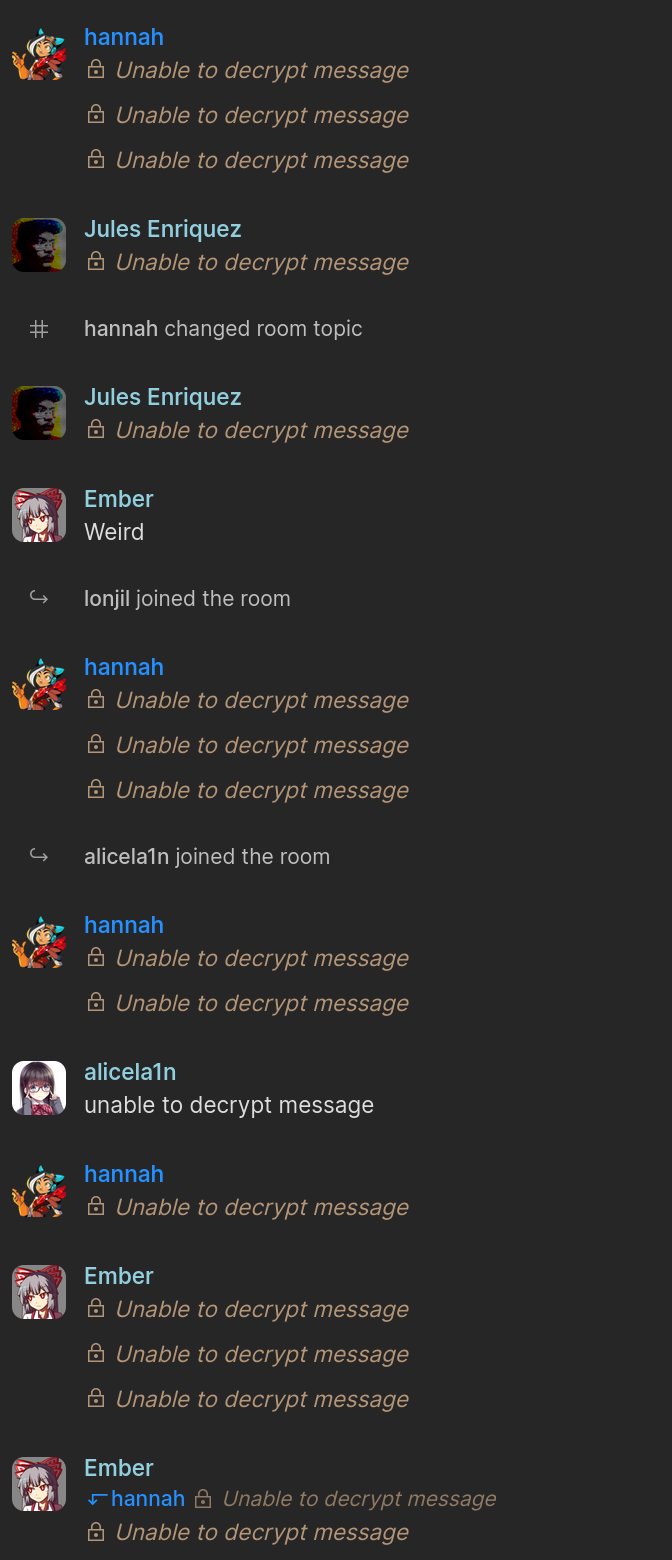
@ariadne Also the fact that which user sent which message is visible even when the message is "Unable to decrypt message" means that at least the author of each message must be unencrypted. And of course it would be possible for an adversary to observe when messages are posted, and I would *guess* also get some indication of their size.
Looooots of interesting and useful metadata swimming around in that data lake…
or as I put it in the Bundernet #known-issues room which is acting as an FAQ
Not true. Lead pipes aren't really a thing here....
@agowa338 i am being dramatic
@ariadne damn, they somehow avoid encrypting _just_ enough an intelligence service could figure out stuff anyways
@ariadne this has always seemed like too many moving parts for something innately vulnerable to a bad actor just screenshotting stuff
@ariadne mAtRiX iS a ViAbLe DiScOrD aLtErNaTiVe
@theorangetheme @ariadne *government beats me with a wrench* well at least they can't force me to disclose my chats, since I can't read them! *government continues beating me with a wrench*
@theorangetheme @ariadne sorry, what's that you say? i can't hear so well anymore since that afternoon the government beat me repeatedly with a wrench
@ariadne I'm glad someone is re-upping how trash matrix is, it really shouldn't get any positive attention at this moment
@froztbyte oh that is not my intention. i think matrix is fine for *unencrypted* chat, when you do not use any software maintained by matrix.org.
@ariadne fair ish I guess, but at a time like this not a lot of nuance will be held "at scale", in the sense of software being tried popularly/widely - "oh what's a matrix? let me try it" path of least resistance is likely to happen for many
I do wish the state of open chat tech was in a .... better place. kinda similar with browsers and engines atm, I guess? not great.
@ZiggyTheHamster @soatok this was just based on 5 minutes worth of observation.
@YKantRachelRead it's not, but it's what is available i guess
@ariadne I mean to be fair if you're a person of interest and they see completely encrypted communications, they're going for the ole rubberhose cryptanalysis anyway. but.
@gothodile no. it is the responsibility of any tool that has so-called "encrypted messenger" functionality to encrypt the metadata too.
@ariadne FYI most of these are on track to get fixed eventually, with the lack of sealed sender probably being the longest horizon. In the meantime, matrix E2EE has already saved me personally one time from a less sophisticated actor - it's just levels of security. Not good enough to protect politically sensitive communication, good enough for a maybe-embarrassing chat with friends
@JadedBlueEyes the problem is that while it may provide sufficient assurance for the scenario you outline (an unsophisticated actor), people will inevitably treat it with the same level of assurance as a tool designed for high assurance communications.
this is because people do not think in terms of assurance, but familiarity.
this is why i tell people to skip matrix E2EE features, because they aren't capable of providing sufficient assurance when you actually *need* the assurance.
also it has the nice benefit that I don't have to hear complaints about screens full of "unable to decrypt message".
@ariadne "you think people would do that? just go on the internet and kill people based on metadata?"
@ariadne try with reactions, IIRC that ones are unencrypted/leaked 🤯
please stop torturing all that people and move them to Delta Chat!
@adbenitez if you are trying to convince me to use delta chat, this is convincing me to publicly shit on it instead. you may want to try a different marketing method.
@ariadne@social.treehouse.systems i believe there's an msc being worked on to resolve unencrypted reactions at least fwiw. no idea on the other stuff
@ariadne@social.treehouse.systems found it, looks like it also fixes the reply references https://github.com/matrix-org/matrix-spec-proposals/pull/4392
also fwiw my girlfriend and i have an e2e encrypted dm and haven't really ran into many issues, all i can think of is sometimes having to wait a bit for keys to sync on a new device but that's it. haven't tried more than a dm though.
@saige cool. i rather chat securely with my girlfriend on Signal, a tool explicitly designed for this.
@ariadne That's a fair enough position, and makes sense for how you're setting things up. However, one person in my timeline suggested turning off e2ee in direct messages, which I think is the exact opposite of what people should be doing, and the danger of this kind of sentiment/advice. In the end, people need to be in the habit of connecting directly using Signal or another known-secure channel when things move off "public" - but in the meantime, keeping things at least mildly secured is a good idea.
@JadedBlueEyes yes, i think we can agree there.
@ariadne I unable to decrypt can't unable to decrypt understand unable to decrypt your unable to decrypt accent. unable to decrypt
@ariadne looks like my xmpp when I log in after 2 weeks
@ariadne Yet you cannot get push notifications when you’re mentioned in an encrypted channel, because IT’S ENCRYPTED. 🤦🏼♂️
@oscherler yes this is what happens when you shoehorn E2EE into something not originally designed for it
@ariadne Are there any good, federated and E2EE IMs? Signal has good E2EE but not federation, XMPP has better federation but no E2EE out of the box.
IMHO, Matrix is currently the best of what we got, in terms of both decentralisation and privacy.
@tapafon when it comes to E2EE federation is not a priority for me, safety is the priority.
@ariadne is this something that could be fixed or is it too fundamental to how Matrix works?
@alwayscurious I'm sure everything is fixable but shoehorning E2EE into something not designed for it will ways play out this way.
@ariadne Yup. My company USES Matrix. And I've seen 'Unable to decrypt message" repeated over and over.
@Chip_Unicorn @ariadne I've only ever seen that myself if you switch to a new device and don't verify the connection (which means you can't read the existing E2E encrypted messages in channels you're in because you haven't validated yet, it's intentional so someone who gets your password can't just log in on a different device and snoop on the channel)
@raptor85 @Chip_Unicorn thank you for explaining matrix's broken E2EE to us. is there anything else you would like to explain to us as a man?
Well, I'd say some public xmpp servers hosted by people actively developing clients or being active in the XSF (xmpp standards foundation) are safe to use, too. For example: conversations.im or yax.im.
Both are listed as default in Monal and I know both admins personally :)
You can of course use any server with Monal.
@ariadne @Chip_Unicorn you would rather people be able to snoop then requiring verification of new devices? Why even bother with encryption at that point?
Just because some people are too incompetent to run updates or follow the prompt to verify after switching to a new device isn't a software bug, it's a clear case of PEBKAC
@raptor85 @Chip_Unicorn the point of the screenshot is not the "unable to decrypt message", but rather the observation that it is leaking all sorts of metadata.
people should use tools *designed* for E2EE messaging if that is what they need, Matrix and XMPP are not this.
@tapafon @ariadne The whole "Metadata" discussion is for the most part FUD by Signal fans.
OFC this doesn't mean I deny the problem.
- But if you are concerned about said issue then you'd already only communicate with you own private self-hosted servers that are only reachable with a VPN over Tor.
The truth is that as of now there are no good options out there, unless you consider sending #PGP-encypted messages to a self-hosted, hidden ntfy.sh server to each other.
But if you are concerned about said issue then you'd already only communicate with you own private self-hosted servers that are only reachable with a VPN over Tor.
Again: Layering & Defining your Scope is critical.
If we expect "#TechIlliterate #Nirmies" to "migrate to #Tails & #GrapheneOS or die" they'll give us all the finger and most likely add a restraint order on top of it.
- OFC we need to work on this scope, but I'd rather offer the "best possible" than being complicit in the Starus Quo.
Feel free to name alternatives that actually work and have actual support…
the scope is that western democracy is in a state of freefall and we are actively losing ground to fascist oligarchs in both the US and EU.
in such a scope, cute toys like OMEMO and IRC's blowfish scripts and things of the same shape like Matrix's OLM/MegOLM do not provide an acceptable level of personal assurance.
telling people to depend on these technologies as a security engineer is malfeasance.
Signal also is not truly good enough (because it is proprietary), but it is at least accessible to non-technical people and cryptographically sound.
the real answer is Tox, but somebody needs to build the plumbing to make it accessible to non-technical people.
@evilpilaf @kkarhan @tapafon Veilid is an application layer, not a messaging layer. But sure, something could be built on Veilid.
@kkarhan @tapafon@soc.ua-fediland.de @ariadne Isn't Tox that P2P thing? There's @cwtch developed by amazing folks like @sarahjamielewis
@tris @kkarhan @cwtch @sarahjamielewis yes. Cwtch would also work, but I am less familiar with it. It also needs plumbing for non-technical people.
BBM worked with fingerprints back in the day because PGP fingerprints were 32-bit at the time. Asking non-technical people to memorize 100s of bits of public key material isn't going to work.
https://blog.tox.chat/2023/03/redesign-of-toxs-cryptographic-handshake/
https://github.com/TokTok/c-toxcore/issues/426
@tapafon @ariadne @monocles @kkarhan sure, but you talked about honeypots and controlled opposition and that's normally not true for the people I mentioned.
Also, albeit a bit philosophical, you always have to trust someone. You seem to make the cut at the client side (so you trust the client developers to not sneak some surveillance code in) and I make the cut somewhere on the server side, not trusting all servers, but some :)
@ariadne Thanks for this thread, it gave me a hearty laugh.
@ainmosni UNABLE TO DECRYPT MESSAGE